On Feb. 20, Microsoft’s security team contacted Commvault regarding suspicious activity observed in its Azure tenant. This cloud instance contained backups of customer data, essential for business continuity. This incident showed signs of escalating into a ransomware attack, with the intent to exfiltrate valuable data for financial gain. However, Commvault’s official disclosure confirmed that “there was no unauthorized access to any data that Commvault protects for any customer.”
In a later update, Commvault clarified that the “threat actor may have accessed a subset of app credentials that certain Commvault customers use to authenticate their M365 environments.” This subtle but critical detail shifted the narrative. The attackers weren’t after the backup data directly; they were after the digital keys used to access customer environments: OAuth tokens.
Those tokens granted cross‑tenant, MFA‑bypassing access to mailboxes, SharePoint sites, and Teams chat, a stealthy supply‑chain route to any organization’s crown jewels.
Commvault’s quick response and patching deserve credit, but the incident exposes a deeper truth: every SaaS‑to‑SaaS integration you enable becomes part of your organization’s attack surface. If you can’t continuously see, assess, and constrain those connections, you can’t manage the risk.
Why are attackers after OAuth tokens?
OAuth tokens are an essential component of modern SaaS integrations. They serve as delegated access keys, enabling applications to act on behalf of users or services without revealing actual credentials. While this makes them extremely powerful for automating workflows and scaling cloud applications, it also makes them a prime target for attackers. Once stolen, these tokens open up a vast array of possibilities for adversaries.
Attackers used Commvault to extract stored credentials used by the Metallic platform to access customer Microsoft 365 environments. These tokens often include scopes that grant broad access to Exchange mailboxes, SharePoint sites, OneDrive files, and even Teams chats. Because these tokens authenticate applications rather than individual users, they bypass user-focused protections like multi-factor authentication, unless organizations enforce additional controls like Conditional Access.
Access tokens typically expire within an hour, but refresh tokens can remain valid for up to 90 days or longer depending on configuration. Many enterprises do not regularly rotate these tokens, which makes them persistently exploitable. Attackers could quietly reuse them to access customer environments without triggering alerts, remaining invisible to most traditional security monitoring solutions.
- OAuth tokens often have elevated privileges due to overly permissive scopes being granted at the time of integration. It’s common to see applications with ReadWrite.All permissions or administrative scopes that are never audited post-deployment. This means a compromised token can serve as a master key, granting not just data access, but potentially allowing changes to tenant-wide settings and user permissions.
- OAuth tokens also facilitate lateral movement. If an attacker gains access to one application, they can sometimes enumerate connected services via the Graph API or other APIs, depending on the token’s granted scopes and the tenant’s configuration. From there, attackers can then request new tokens, or exploit existing integrations to deepen their access and expand the attack. Their ability to pivot move across apps and tenants without triggering MFA or interactive login anomalies makes OAuth token theft particularly dangerous in cloud-native environments.
Few organizations have robust monitoring for app-to-app API calls. Traditional CASBs and endpoint detection systems focus on user behavior, not on the autonomous activity of authorized integrations. This creates a significant blind spot that adversaries are increasingly exploiting.
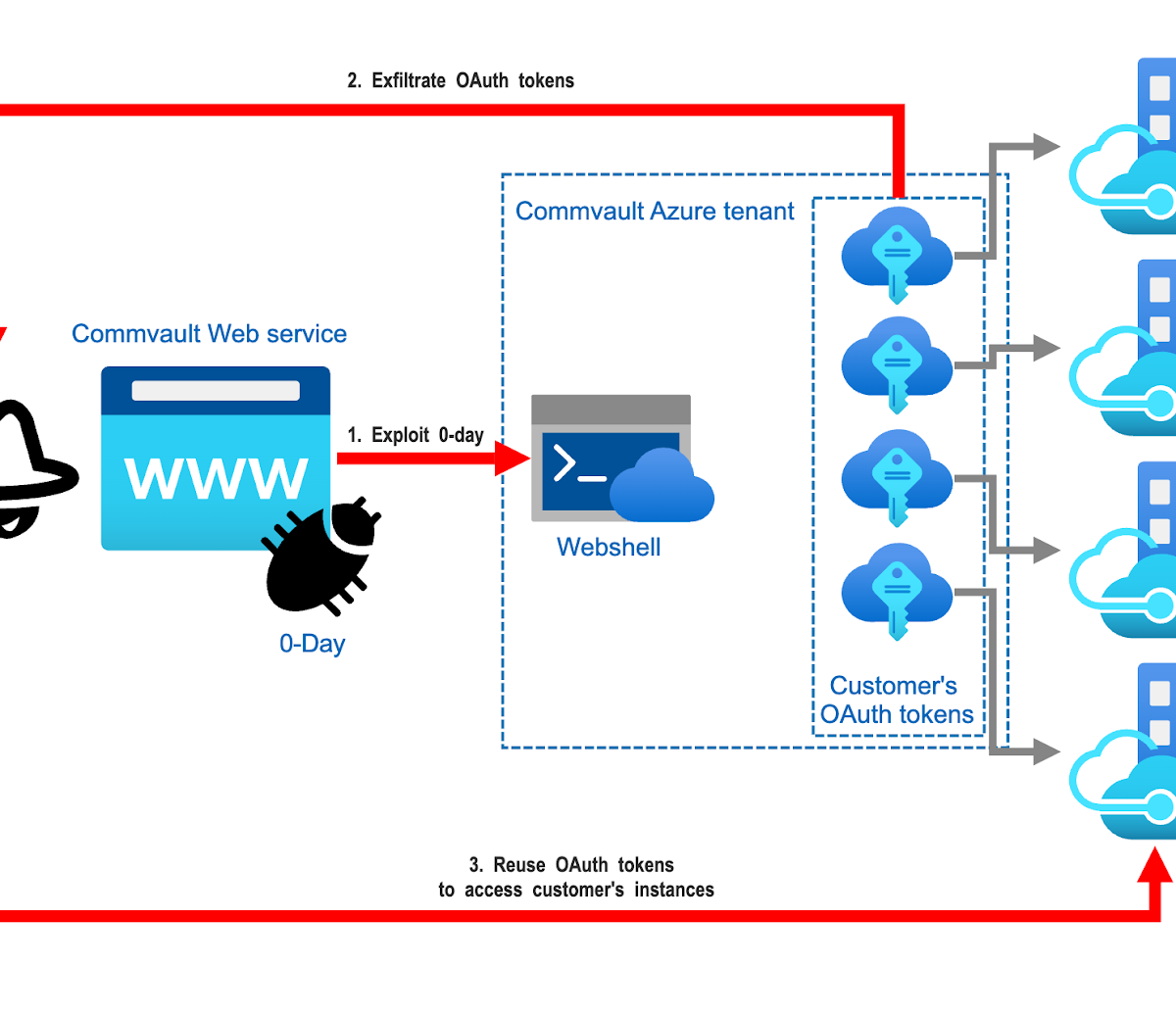
Kill chain: From zero-day exploit to tenant access
Attackers began by exploiting a zero-day vulnerability in the Web Server component of Commvault’s Metallic SaaS platform (CVE-2025-3928). This flaw, which impacted Commvault’s Azure-hosted infrastructure, allowed authenticated users to upload and execute web shells. This includes malicious scripts capable of running arbitrary commands. By doing so, attackers gained persistent, system-level access to Commvault’s environment.
From this foothold, the attackers could quickly target high-value internal assets such as configuration stores or credential vaults. While Commvault has not disclosed the exact method of credential access, its advisory confirms that OAuth credentials used to authenticate with customer Microsoft 365 tenants were exposed. Originally provisioned for backup purposes, these credentials were likely stored in a manner that allows reuse.
Once the attackers had access to these credentials, they were able to impersonate Commvault’s applications and access data in affected Microsoft 365 tenants. OAuth tokens typically carry elevated privileges, such as Mail.ReadWrite and Sites.FullControl.All, and because they authenticate applications, not users, they bypass protections like MFA.
From this position, the attackers could have moved laterally by using Graph API calls to enumerate tenants, users, and connected applications, depending on the granted scopes and tenant configuration. In environments where Microsoft 365 acts as a central SaaS hub, such access could enable compromise of additional services like Salesforce, ServiceNow, or Box. This activity would have blended in with authorized service principal activity and thus likely evaded detection by traditional, user-focused monitoring tools. Because many organizations lack full visibility into app-to-app behavior or service principal activity, attackers can exploit these security gaps to maintain stealth and persistence.
When combined with the misuse of powerful OAuth credentials, a single cloud vulnerability can cascade into a broad supply chain compromise affecting hundreds of downstream environments.
Commvault breach: A classic supply chain attack
This breach underscores how a single SaaS integration can act as a supply chain vulnerability, silently exposing hundreds of downstream tenants. The kill chain from a zero-day exploit to token theft, token replay, and eventual lateral movement, reveals that your security perimeter doesn’t end with your login portal. Instead, it extends into every integration you authorize.
This type of attack also falls under the broader category of supply chain compromises. Just like the infamous SolarWinds breach, where attackers inserted malicious code into widely deployed IT management software to reach thousands of targets, the Commvault incident reveals the dangerous potential of compromising a single trusted vendor. If you want to compromise a single tenant, you target their credentials. But if you want access to hundreds, you go after the platform that already has trusted access to all of them.
Supply chain attacks exploit trust. They target the interconnectedness of modern IT ecosystems, and when the chain breaks at any one link, the blast radius can be enormous. Every SaaS integration is not just a convenience, it’s a potential conduit for attack. Monitoring, auditing, and securing these pathways is no longer optional.
How AppOmni secures organizations against these risks
In its official advisory, CISA emphasized the risk to downstream tenants from the compromise of Commvault’s SaaS platform. It warned that the stolen OAuth credentials may still be active in many customer environments and highlighted the need for immediate credential rotation and increased SaaS-to-SaaS monitoring. CISA specifically called out the challenge of detecting lateral movement across cloud-connected systems and the danger of app-to-app access pathways.
AppOmni’s platform is uniquely equipped to respond to the challenges CISA outlines. It delivers critical visibility and security controls across the SaaS stack, not only for users, but also for the applications and credentials that operate on their behalf. What follows is a breakdown of how AppOmni directly maps to the key phases of the Commvault attack and the core recommendations in the CISA alert.
The Commvault incident clearly illustrates the hidden dangers of unmanaged SaaS-to-SaaS integrations and more specifically, the significant risks tied to OAuth tokens. AppOmni is purpose-built to address exactly this type of threat vector. It provides continuous visibility, automated enforcement, and real-time detection across the SaaS ecosystem.
Here’s how AppOmni could have prevented, detected, or significantly mitigated this breach:
Continuous OAuth and SaaS integration inventory
AppOmni discovers every connected application across your environment, including those long forgotten or set up by users without security oversight. It maps every OAuth token, API key, and service principal to their exact permission scopes, identifying excessive privileges or stale credentials before they can be abused. Had Commvault’s customers been using AppOmni, they would have had a real-time inventory of every token granted to Metallic with clear insight into what each one could access.
Blast-radius visualization
When a token is compromised, time is of the essence. AppOmni’s blast-radius visualization tools show which data repositories are exposed through each token or app. Security teams can instantly answer the question: “If this token is abused, what’s at risk?” In a situation like Commvault’s, affected customers would have been able to scope the damage in minutes, not days.
Real-time threat detection
AppOmni doesn’t just observe static configuration, it monitors behavior in real time. Key detections include:
- Entra Unified Audit – New Service-Principal Credentials Added: Immediate alerts when attackers add unauthorized credentials, a key indicator of ongoing infiltration attempts.
- Unusual Updates to ServicePrincipalCredential: Rapid detection of suspicious credential modifications, potentially indicative of a breach.
- Token Replay Alerts: Detection of OAuth tokens being reused from unknown or suspicious locations, helping organizations promptly respond to token compromise incidents.
Policy enforcement & remediation guidance
Organizations can define and enforce rigorous policies, including regular OAuth token rotations and controlled access permissions. AppOmni integrates seamlessly with popular collaboration tools, automating remediation actions to contain threats quickly and effectively.
Audit-ready documentation
AppOmni maintains comprehensive records of SaaS security events, providing critical documentation for compliance audits, such as FedRAMP, ISO 27001, and GDPR. For companies exploring complex web of SaaS integrations, AppOmni offers more than visibility, it offers peace of mind.
We’re here to help. If you’re interested in better understanding how this breach happened and how it could have been prevented, don’t hesitate to connect with us.
Related Resources
-

Discover what went wrong in the Commvault breach: How AppOmni’s powerful SaaS security platform steps in to stop threats before they strike.
-

Learn how OAuth phishing works, why it’s harder to detect than traditional attacks, and how to protect your accounts from unauthorized access.
-

In this blog, we take a look at the most impactful SaaS security incidents in 2024 and share insights on what to expect in 2025 for SaaS security.
The post OAuth Tokens: The Danger Behind the Commvault Breach appeared first on AppOmni.
*** This is a Security Bloggers Network syndicated blog from AppOmni authored by Martin Vigo, Lead Offensive Security Engineer, AppOmni. Read the original post at: https://appomni.com/ao-labs/oauth-tokens-danger-behind-commvault-breach/